Comprehensive IT Solutions: Customized to Satisfy Your Needs
Looking for IT services that are tailored to satisfy your certain demands? Look no more. Our thorough IT options are created with you in mind. We recognize your needs and customize our services to fit your organization perfectly. From implementing efficient IT infrastructure to enhancing information security as well as personal privacy, we have actually obtained you covered. With our expertise, we'll maximize IT performance and scalability, ensuring your technology operates at its finest. Get all set to experience IT services that are absolutely individualized for you.
Recognizing Your IT Demands
To comprehend your IT needs, you'll require to assess the current capacities of your systems and recognize any kind of potential voids or areas for renovation. By examining your existing systems, you can establish what is functioning well and what needs to be enhanced or replaced.
During this process, it is essential to include key stakeholders within your organization. This includes IT employees, department heads, as well as end-users who depend on the systems daily (Managed IT Services). By soliciting their input as well as comprehending their discomfort factors, you can get a far better understanding of the specific IT requirements that need to be attended to

Along with examining the present abilities of your systems, it is additionally crucial to identify any type of prospective spaces or locations for renovation. This might include out-of-date equipment or software application, inefficient procedures, or poor security measures. By determining these gaps, you can focus on the locations that require immediate focus and also allocate sources appropriately.
Inevitably, by comprehending your IT demands through a comprehensive analysis, you can make educated decisions concerning the most effective solutions to carry out. This will certainly make sure that your IT facilities is maximized to satisfy your company's special needs and also sustain your general service purposes.
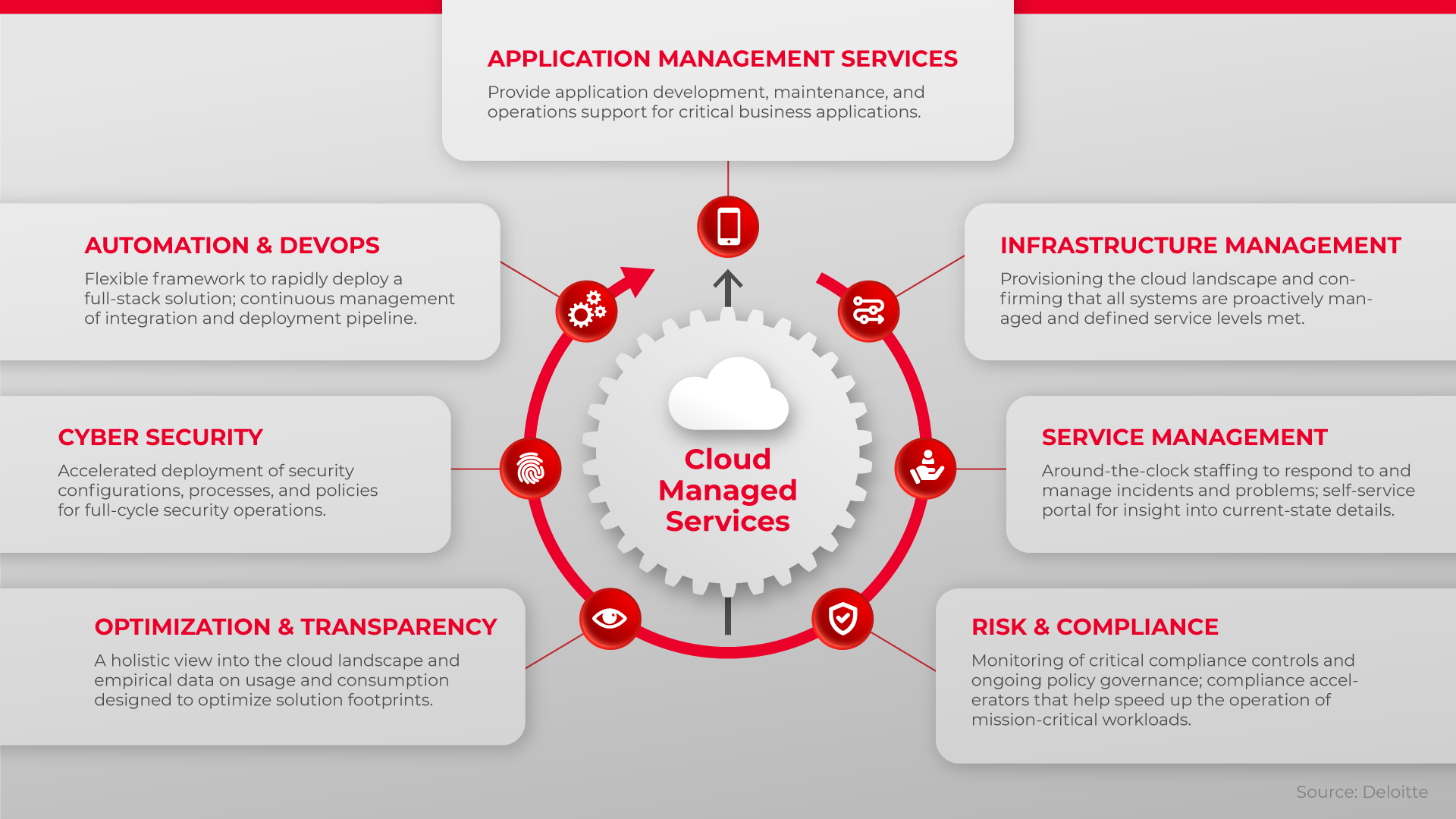
Tailoring IT Solutions for Your Company
Tailoring IT options for your company involves creating a special strategy that fits your specific demands. With the ever-changing technical landscape, it is crucial for companies to adapt and customize their IT remedies to remain competitive. By customizing your IT solutions, you can make certain that your organization's requirements are met effectively and also efficiently.
One of the vital benefits of personalizing IT services is that it enables you to address your company's one-of-a-kind difficulties as well as objectives. Off-the-shelf solutions may not completely fulfill your demands, yet with a personalized plan, you have the versatility to integrate functions as well as capabilities that are customized to your specific needs. This can result in enhanced performance, streamlined procedures, and enhanced overall efficiency.
Tailoring IT services additionally enables you to straighten innovation with your business goals. By working closely with IT specialists, you can determine the locations that need improvement as well as develop a strategy that straight supports your lasting objectives. This customized technique makes certain that your IT framework is enhanced to fulfill your company's details demands, supplying a solid foundation for growth and success.
In addition, customizing IT remedies provides you higher control and also scalability. You can choose the components and systems that ideal fit your company's requirements, permitting smooth assimilation and also simple monitoring. As your business evolves, you have the adaptability to scale up or down your IT services, guaranteeing that they remain to straighten with your changing requirements.

Applying Efficient IT Infrastructure
Implementing reliable IT framework includes developing a strong structure that supports your organization's technological needs as well as objectives. It is crucial to have a durable as well as properly designed framework in area to make sure smooth procedures and take full advantage of productivity. With the rapid advancements in modern technology, having an efficient IT infrastructure has ended up being more vital than ever before.
To begin, you should assess your company's demands and also develop an extensive plan that aligns with your objectives - Cyber Security. This includes evaluating your current systems, determining any kind of gaps or locations for renovation, and identifying the necessary resources and innovations needed to address them
Next off, you require to select the best software and hardware solutions that will sustain your company's one-of-a-kind demands. This implies selecting dependable servers, network equipment, and also storage space devices that can manage your applications as well as data efficiently. Additionally, carrying out the suitable software go to these guys application applications and also tools will allow your staff members to work much more efficiently and also work together successfully.
Incorporating security measures into your IT framework is critical to safeguard your company's delicate data and systems. This includes applying firewalls, antivirus software application, and also file encryption modern technologies to secure versus possible cyber dangers.
Finally, recurring monitoring as well as upkeep are vital to make certain optimum performance and also minimize downtime. Routine upgrades as well as updates will certainly keep your framework approximately day and also durable, allowing your organization to remain in advance in the ever-evolving technology landscape.
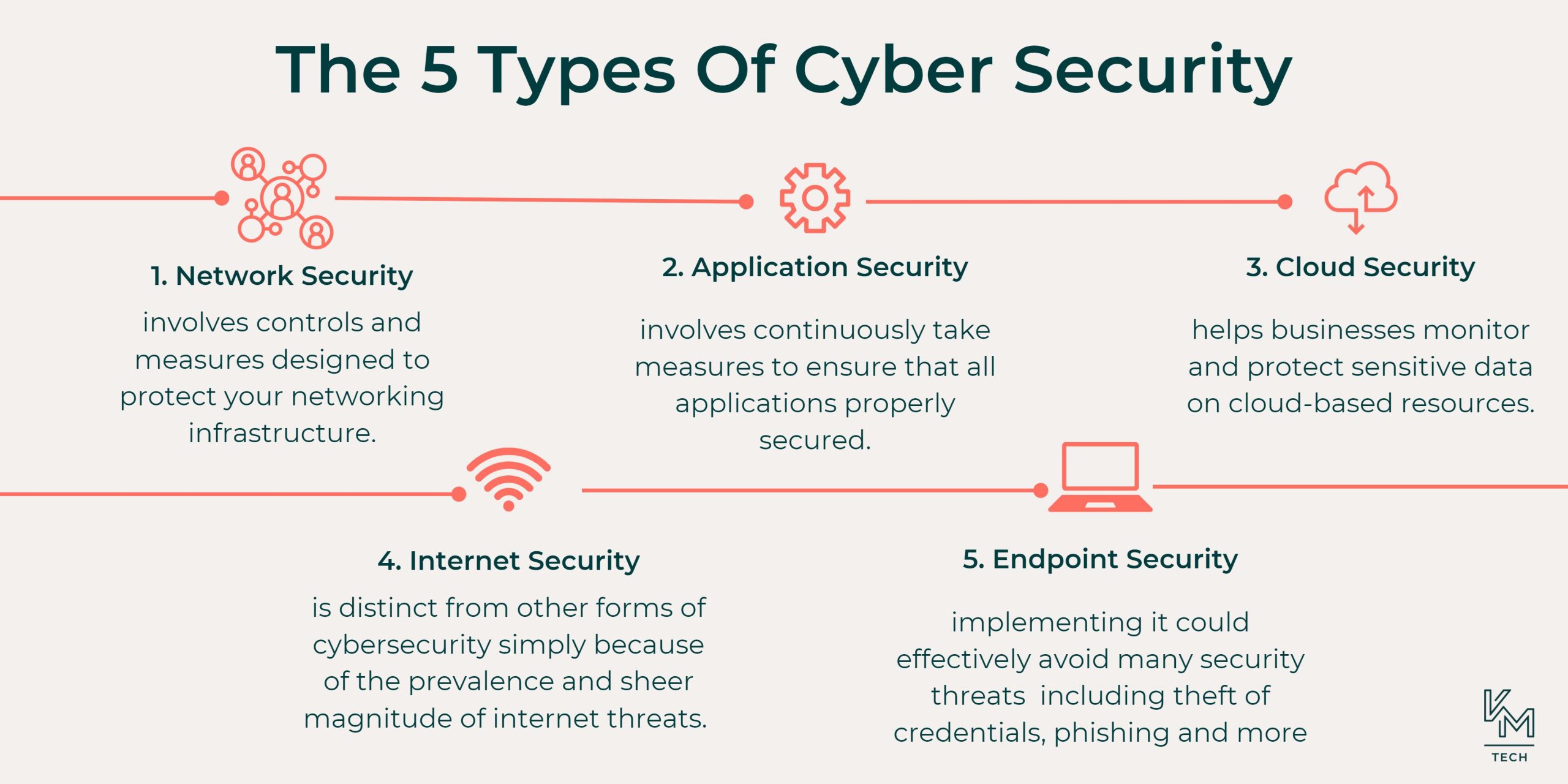
Enhancing Data Security and also Privacy
To improve data safety as well as privacy, you ought to regularly update your antivirus software program and execute encryption technologies to protect against prospective cyber risks. By maintaining your anti-virus software as much as date, you make certain that your computer is secured against the current infections, malware, and various other destructive software application. Normal updates make sure that your anti-virus program has the most recent infection meanings and also safety and security patches, supplying you with the most effective possible protection.
Encryption modern technologies are one more crucial tool in protecting your information. By encrypting your documents, you make it hard for unapproved individuals to gain access to and also comprehend your sensitive information. Encryption transforms your data right into a secret code, making it unreadable without the file encryption key. In this manner, even if your information is obstructed, it view continues to be safe and secure.
Furthermore, it is crucial to use strong, one-of-a-kind passwords for all your accounts as well as alter them routinely. Passwords should include a mix of capital as well as lowercase letters, numbers, and also special personalities. Utilizing a password manager can help you create and also remember intricate passwords.

Ultimately, beware when sharing personal info online. Prevent clicking on dubious web links or downloading files from unidentified resources. Phishing attacks as well as visit malware frequently disguise themselves as reputable websites or email add-ons.
Optimizing IT Efficiency and Scalability
By enhancing IT efficiency and also scalability, you can ensure that your systems are running effectively and can manage raising needs. With the constantly progressing technical landscape, it is critical to keep your IT infrastructure as much as date as well as versatile. By doing so, you can maximize productivity, decrease downtime, as well as remain in advance of the competitors.
One means to maximize IT efficiency is via normal system updates and also software program spots. These updates not just boost system capability yet likewise attend to any type of possible vulnerabilities. By remaining on top of updates, you can improve system safety and also make sure that your procedures run smoothly.
Scalability is one more important element to take into consideration. As your company grows, so do your IT requires. By carrying out scalable options, you can quickly fit the raised demands without jeopardizing performance. This flexibility permits you to scale your IT framework as required, whether it's adding more storage space, updating servers, or expanding network ability.
Additionally, maximizing IT efficiency and scalability involves monitoring as well as analyzing your systems' efficiency. By proactively determining bottlenecks or locations of improvement, you can make essential modifications and protect against possible problems before they influence your operations.
Verdict
So, now you have a clear understanding of how detailed IT solutions can be customized to meet your special needs. By customizing IT options for your company, executing reliable IT infrastructure, boosting data safety and also privacy, as well as optimizing IT performance as well as scalability, you can ensure that your IT systems are effective, safe, and able to support your service development. With the right IT services in position, you can concentrate on your core company goals, recognizing that your technology needs are cared for.
By tailoring your IT options, you can make sure that your organization's needs are fulfilled properly as well as effectively.
Off-the-shelf solutions might not totally fulfill your requirements, yet with a tailored plan, you have the flexibility to incorporate functions as well as performances that are tailored to your certain requirements. As your service progresses, you have the adaptability to scale up or down your IT remedies, guaranteeing that they proceed to line up with your altering requirements.
Next, you need to select the right hardware and software remedies that will certainly sustain your company's distinct demands. Currently you have a clear understanding of just how detailed IT options can be tailored to meet your unique demands.